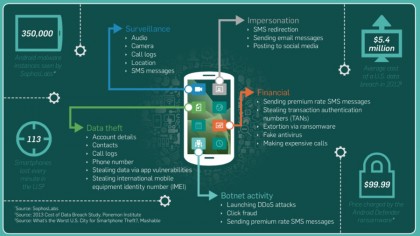
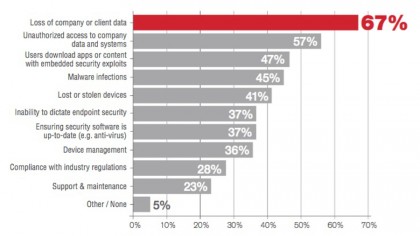
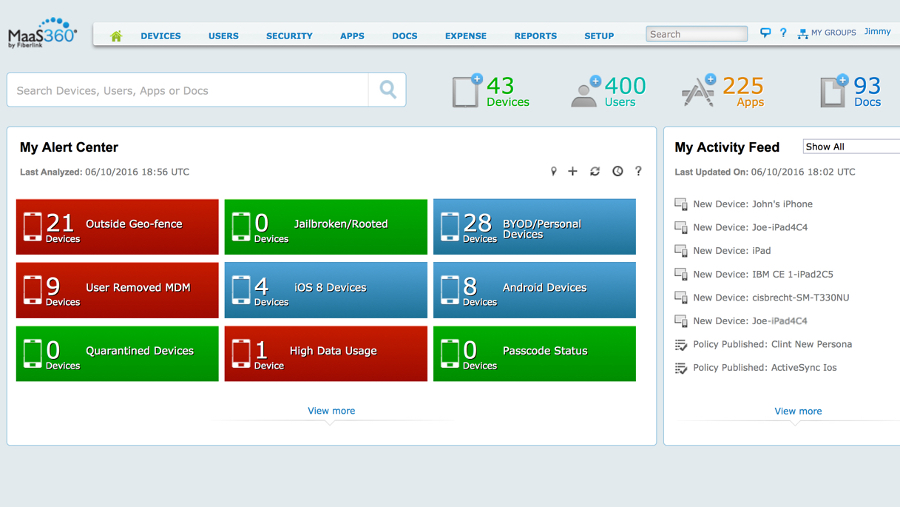
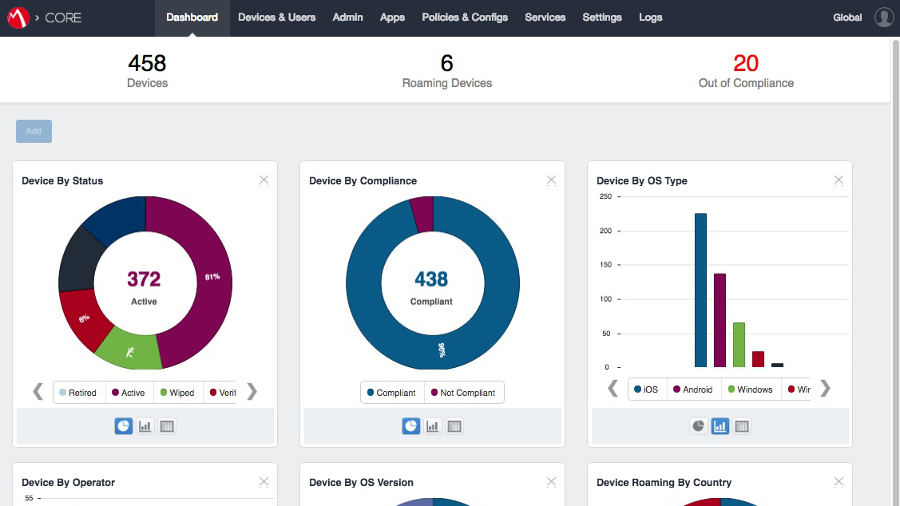
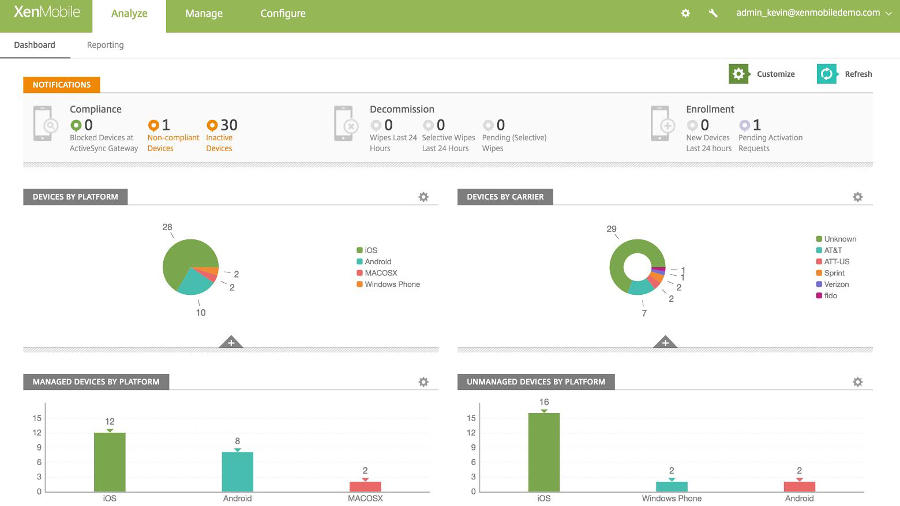
As the cloud continues to become a commercial imperative for businesses, they have realised they must overhaul their data backup processes.
The data within your business is its most precious commodity. As such it is vital that the backup systems in place are robust enough to cope with not only your data backup needs today, but for the future.
When choosing a cloud backup provider, aside from the price, the user should pay attention to presence of the following functionalities:
- These are the best cloud storage providers in the market.
- Want to store and share big files in the cloud? We did the legwork for you
- Check out the best cloud storage for photos and pictures
- Provide not only Cloud but Hybrid Backup as well of the user has sensitive data or data he/she cares about a lot, he/she must be sure that the cloud backup provider also has a functionality to backup up the data locally and on various media.
- Protection for All devices most households and businesses deal with a myriad of devices - a computer, laptop, iPhone, etc - and a combination of different platforms - a Mac and a PC, an iPhone and an Android. The backup solution should protect all these devices and the various brands.
- Web Access from Any Device the user should ensure of always having access to the files backed up to the cloud from any device.
- Full-Image Backup and Recovery this means that the operating system, applications, history, preferences, photos, files, videos, bookmarks, all settings and customizations including license keys and passwords — everything, should be backed up to the cloud and locally. If everything is backed up, it can later be recovered to bare metal and a fully bootable state.
- File and Folder Backup and Recovery the user needs to be able to backup and recover a single file or folder. Then, the user should also be able to search cloud backups to quickly find and recover exactly what is needed.
- Incremental Social Backup accidental deletion and social network errors can erase your memories and photos from Facebook forever, that’s why it would be nice if the cloud backup can backup Facebook, Instagram and more.
- Multiple Backup Plans the user needs to be able to schedule as many different backup plans as needed.
- Encryptions and Passwords it is important to be able to encrypt data on the computer before sending it to the secure cloud. This ensures maximum privacy and keeps the data safe.
What about businesses?
When selecting a cloud provider, it is important that you compare them against your key criteria: availability, pricing, performance, security etc. What is your organisation seeking to achieve with cloud, in terms of use cases or cost efficiencies? Select a provider or providers that enable you to extract the greatest business value today and down the road as your business requirements evolve.
- Investigate multi-cloud strategies. Apart from cost or operational efficiencies, there’s a business continuity aspect to examine. When organisations run applications on multiple cloud services rather than relying on a single vendor, they reduce the risk of a vendor’s service outage causing them significant issues and downtime.
- Ensure your provider allows you to generate and manage encryption keys exclusively. A good cloud provider should offer various storage tiers to deliver cost efficiencies for various data types and offer the ability to automate the process.
- Ensure your provider enables to create a Virtual Private Cloud (VPC) that is completely private to the customer.
- Check the cost structure. Chose a provider that offers a flexible and cost-effective solution. A good cloud provider should offer various storage tier so that data is automatically moved data to the most cost-effective access tier based on access patterns, without impacting performance or operational overhead.
- Evaluate private/on-premises options that provide the same levels of scale and cost efficiencies while maintaining all data locally.
Safety steps
There are a number of easy-to-follow steps to ensure your data is safe when it moves to the cloud:
- Look at your existing service level agreements. Often SLAs were written and signed in the pre-cloud period. Levels of accessibility, data backup responsibilities and ownership all need to the reconsidered for a cloud-based environment.
- Does your existing service scale? One thing is certain: your current cloud storage capacity will be out stripped by your actual needs. As big data becomes more important for businesses, ensure your data backup service can scale as your needs expand.
- Security is of paramount importance. SLAs must cover in detail the security that your cloud backups will use. This should include the security of the data centre itself, but also the security of your data as it moves from your business, over the internet and onto your backup service provider's servers.
- When disaster strikes, a good data backup service is only as good as its recovery options. If your business did lose on-site data, how would your business recover these files? Look for a backup service that has redundancy built into its data centres and also offers other means of shipping your lost files to your premises.
- Think about physical security. As your business is backing up its data off-site, how safe and secure is your cloud partner's data centre? Many data centres are in disused nuclear bunkers, but many are not, so look closely at the physical security of their data centre premises.
- Ronan McCurtin, senior sales director at Acronis for Northern Europe and Sabo Diab, VP Global Marketing at CTERA networks have contributed to this feature.